Okta SCIM Integration
System for cross-domain identity management (SCIM) can be used to automatically provision and de-provision members and groups in your Bitwarden organization.
note
SCIM Integrations are available for Teams and Enterprise organizations. Customers not using a SCIM-compatible identity provider may consider using Directory Connector as an alternative means of provisioning.
This article will help you configure a SCIM integration with Okta. Configuration involves working simultaneously with the Bitwarden web vault and Okta Admin Portal. As you proceed, we recommend having both readily available and completing steps in the order they are documented.
The following provisioning features are supported by this integration:
Push Users: Users in Okta that are assigned to Bitwarden are added as users in Bitwarden.
Deactivate Users: Users with the deactivated status will no longer have access to their assigned apps. Deactivating a user in Okta will change their Bitwarden status to revoked.
Delete user: Users deleted in Okta will be moved to revoked status in the Bitwarden organization.
note
Choosing the suspended status for a user in Okta will not result in a revoked status in Bitwarden.
Push Groups: Groups and their users in Okta can be pushed to Bitwarden.
note
Please note, Bitwarden does not support changing a user's email address once provisioned. Bitwarden also does not support changing a user's email address type, or using a type other than primary. The values entered for email and username should be the same. Learn more.
note
Are you self-hosting Bitwarden? If so, complete these steps to enable SCIM for your server before proceeding.
To start your SCIM integration, open the Admin Console and navigate to Settings → SCIM provisioning:
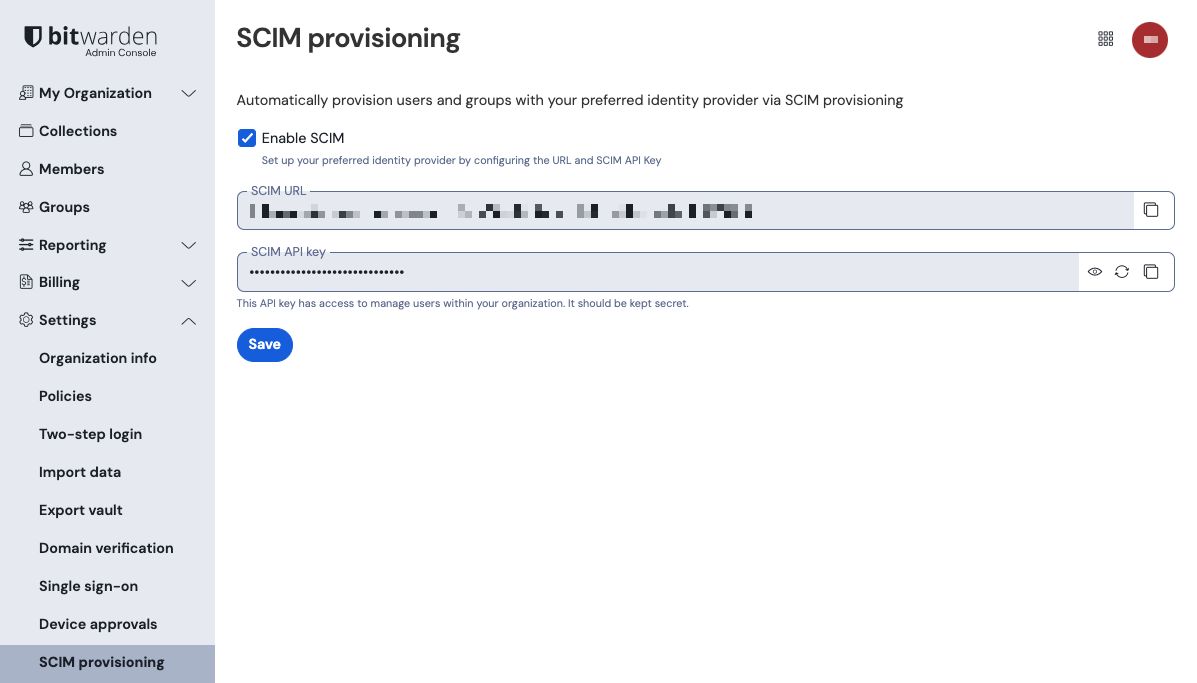
Select the Enable SCIM checkbox and take note of your SCIM URL and SCIM API Key. You will need to use both values in a later step.
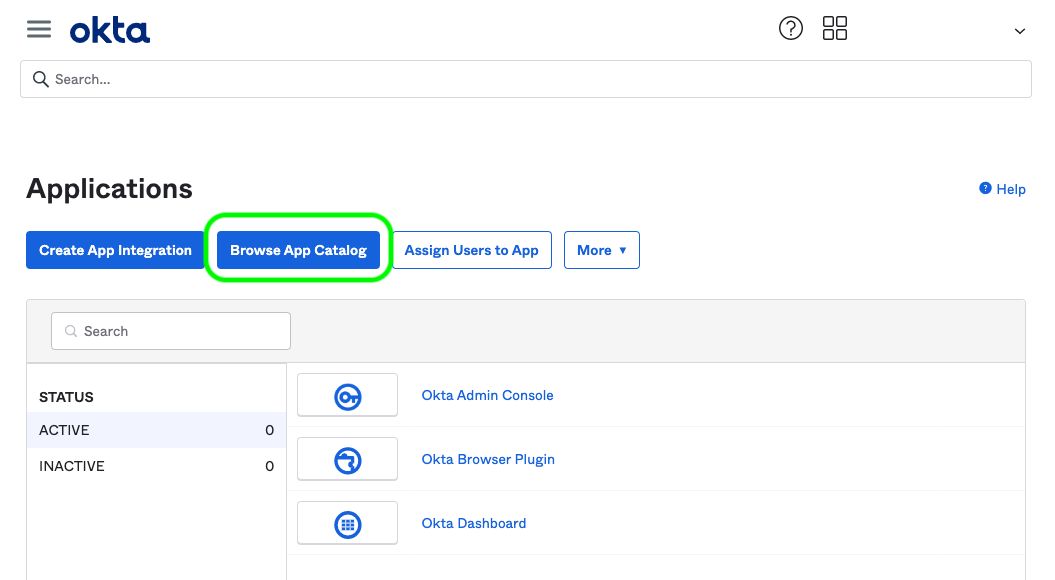
In the Okta Admin Portal, select Applications → Applications from the navigation. On the Application screen, select the Browse App Catalog button:
In the search bar, enter Bitwarden and select Bitwarden:
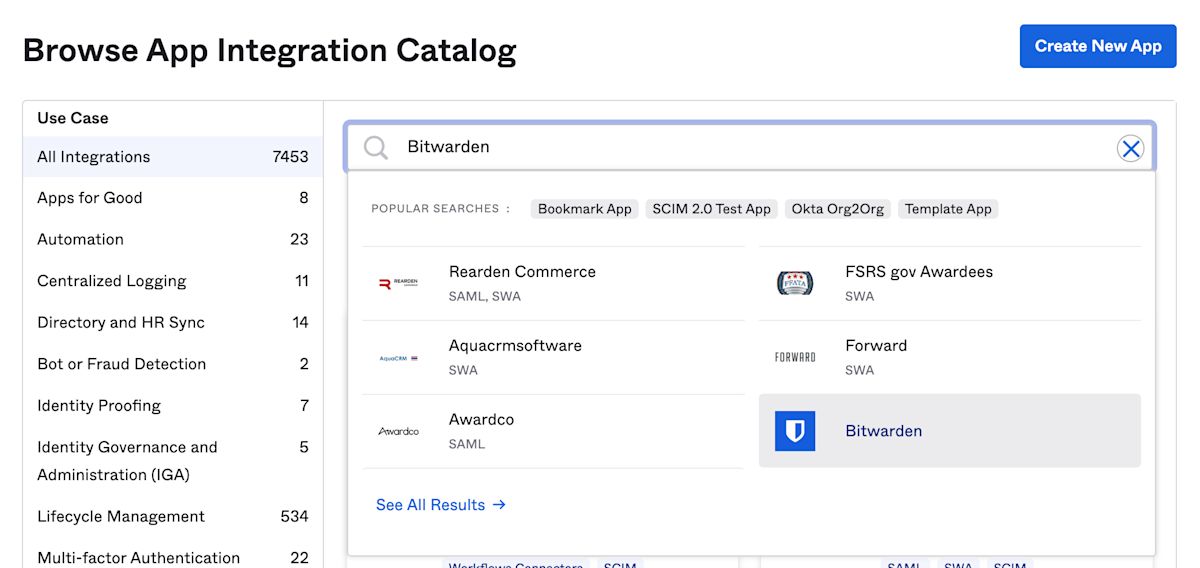
Select the Add Integration button to proceed to configuration.
On the General Settings tab, give the application a unique, Bitwarden-specific label. Check the Do not display application icon to users and Do not display application icon in Okta Mobile App options and select Done.
To setup provisioning, the following steps must be completed in the order presented.
Open the Provisioning tab and select the Configure API Integration button.
Once selected, Okta will list a few options for you to configure:
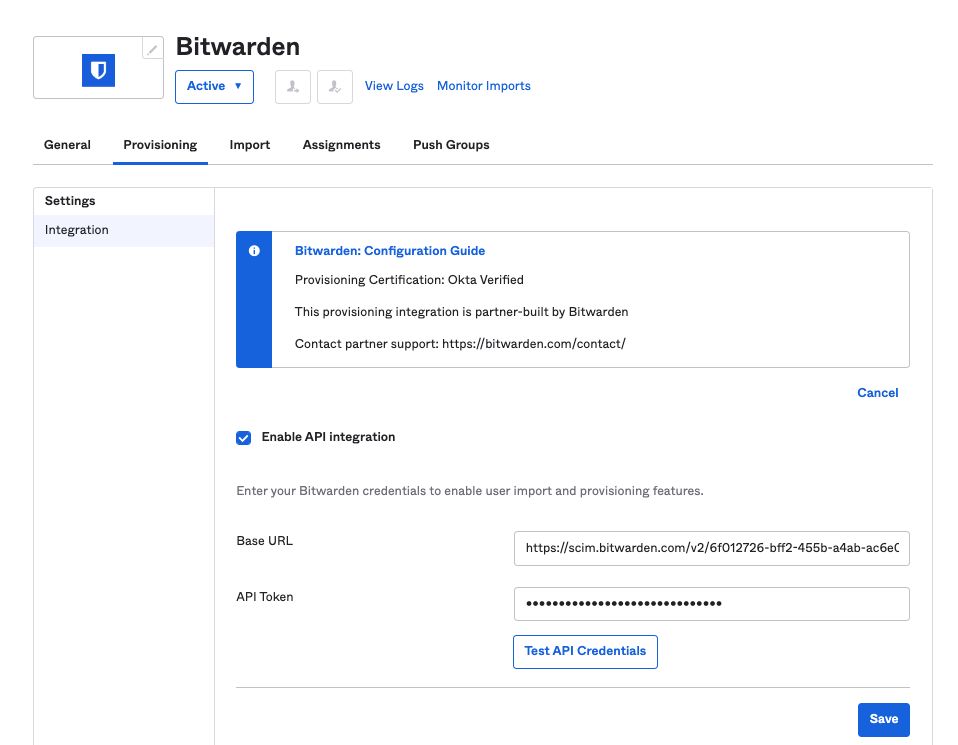
Check the Enable API Integration checkbox.
In the Base URL field, enter your SCIM URL, which can be found on the SCIM Provisioning screen (learn more).
In the API Token field, enter your SCIM API Key (learn more).
Once you are finished, use the Test API Credentials button to test your configuration. If it passes the test, select the Save button.
After the provisioning settings step has been completed, navigate to the Provisioning → To App screen. Then, select the Edit button:
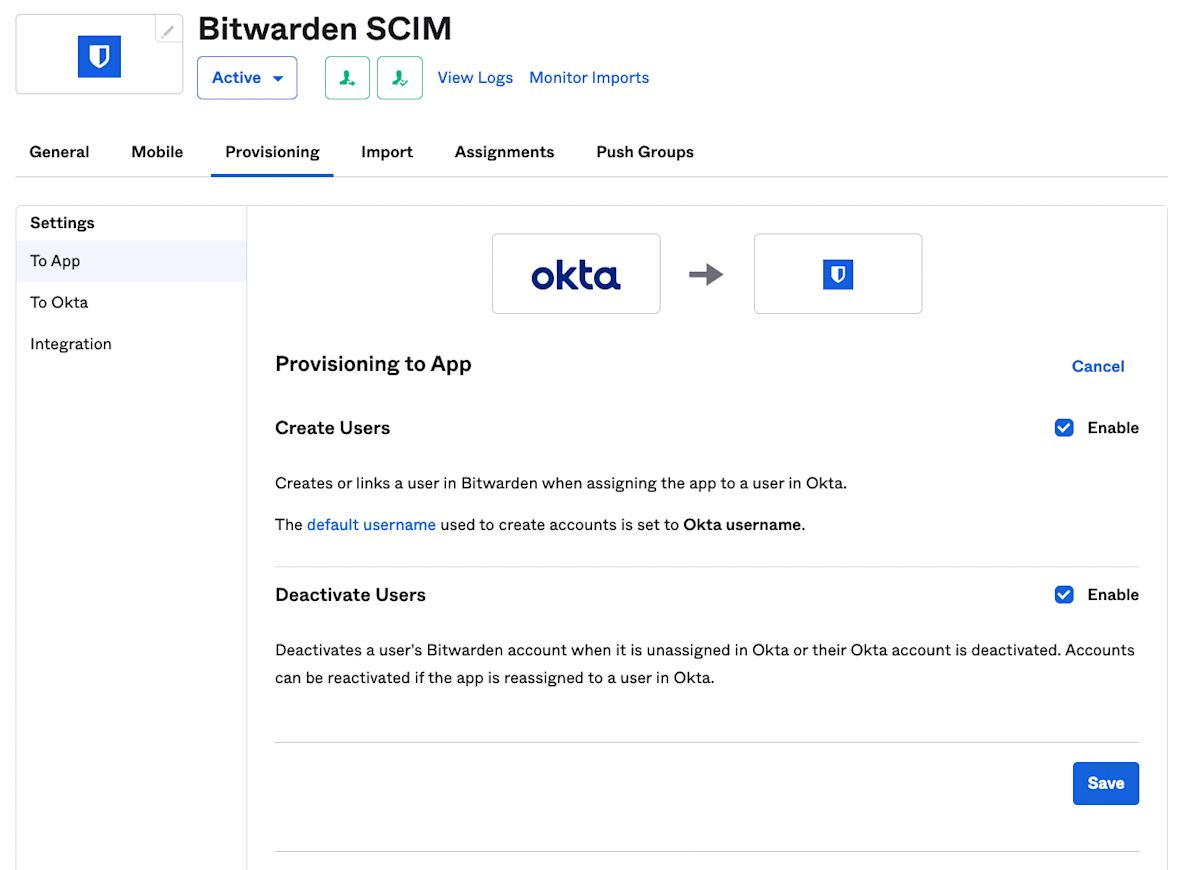
Enable, at a minimum, Create Users and Deactivate Users. Select Save when you are done.
Open the Assignments tab and use the Assign dropdown menu to assign people or groups to the application. Assigned users and groups will be automatically issued an invitation. Depending on your workflow, you may need to use the Push Groups tab to trigger group provisioning once they are assigned.
Now that your users have been provisioned, they will receive invitations to join the organization. Instruct your users to accept the invitation and, once they have, confirm them to the organization.
note
The Invite → Accept → Confirm workflow facilitates the decryption key handshake that allows users to securely access organization vault data.