Secrets Manager Quick Start
tip
If you're a developer, you may prefer Developer Quick Start. The article you're currently on will cover Secrets Manager from an administrative and setup point of view.
Bitwarden Secrets Manager enables developers, DevOps, and cybersecurity teams to centrally store, manage, and deploy secrets at scale.
The Secrets Manager web app will be your home for setting up your secrets management infrastructure. You'll use it to add and organize secrets, create systems of permissions to fit your needs, and generate access tokens for use by your applications. Once complete, you'll move on to the Developer Quick Start guide to learn how to inject secrets into your machines and applications.
You must be an organization owner to enable Secrets Manager. To start using Secrets Manager:
In the Admin Console, navigate to your organization's Billing → Subscription page.
In the More from Bitwarden section, select the Subscribe to Secrets Manager checkbox.

Add Secrets Manager
Once activated, Secrets Manager will be available through the web app using the product switcher:
Before your take your first steps with Secrets Manager, you will need to explicitly invite a few organization members to join.
tip
Before proceeding, we recommend setting up one or more groups for users of Secrets Manager. You will need to give members access to Secrets Manager through the Members page, but you can use groups to scaleably assign access to secrets once your vault is populated.
To give members access to Secrets Manager you must be an organization owner or admin:
Open your organization's Members view and select the members your want to give access to Secrets Manager.
Using the menu, select Activate Secrets Manager to grant access to selected members:

note
Once Secrets Manager access has been granted to a user (or yourself), you may need to refresh the vault in order for Secrets Manager to appear in the product switcher.
From your organization's Billing → Subscription page you will be able to assign total allowed user seats and machine accounts for your Secrets Manager organization.
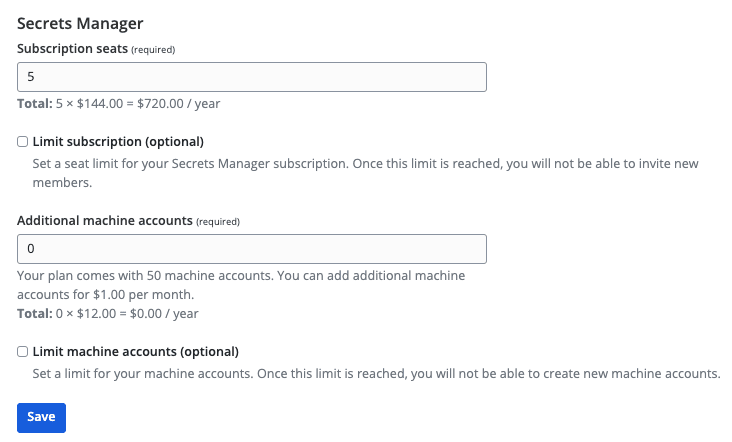
Secrets Manager will automatically scale your user seats and machine accounts when new users or machine accounts are added. A limit can be set by selecting the Limit subscription and Limit machine accounts boxes.
note
In the User seats field, the specified number must be lower than or equal to the number of seats specified for your Password Manager subscription.
You can also use the Additional machine accounts field to explicitly add machine accounts above your plans pre-packaged number; 20 for Teams and 50 for Enterprise.
Use the product switcher to open the Secrets Manager web app. If this is your first time opening the app you'll have an empty vault, but eventually it'll be full of your projects and secrets:

Let's start filling your vault.
Projects are collections of secrets logically grouped together for management access by your DevOps, cybersecurity, or other internal teams. It's important to take into account, when creating your projects, that projects will be the primary structures through which you assign members access to secrets. To create a project:
Use the New dropdown to select Project:

Create a project Enter a Project name.
Select the Save button.
Adding organization members to your project will allow those users to interact with the project's secrets. To add people to your project:
In the new project, select the People tab.
From the People dropdown, type or select the member(s) or group(s) to add to the project. Once you've selected the right people, use the Add button:

Add people to a project Once members or groups are added to the project, set a level of Permissions for those members or groups. Members and groups can have one of the following levels of permission:
Can read: Members/groups will be able to view existing secrets in this project.
Can read, write: Members/groups will be able to view existing secrets and create new secrets in this project.
Now that you have a project with a handful of members who can help you manage it, let's add some secrets to the project. Secrets are sensitive key-value pairs stored in your vault, typically things that should never be exposed in plain code or transmitted over unencrypted channels, for example:
API Keys
Application Configurations
Database Connection Strings
Environment Variables
You can import secrets directly to your vault as a .json file or add secrets manually:
To import your secrets:
Review this document for help properly formatting an import file.
Select Settings → Import data from the left-hand navigation:

Import data Select Choose File and choose a
.jsonfile for import.
To add secrets manually:
Use the New dropdown to select Secret:

Create a secret In the New Secret window's top-most section, enter a Name and Value. Adding Notes is optional.
In the Project section, type or select the project to associate the secret with. A few key points:
Each secret can only be associated with a single project at a time.
Only organization members with access to the project will be able to see or manipulate this secret.
Only machine accounts with access to the project will be able to create a pathway for injecting this secret (more on that soon).
When you're finished, select the Save button.
Repeat this process for as many secrets as you want to add to your vault.
Now that you've got a project full of secrets, it's time to start constructing machine access to those secrets. Machine accounts represent non-human machine users, or groups of machine users, that require programmatic access to some of the secrets stored in your vault. Machine accounts are used to:
Appropriately scope the selection of secrets a machine user has access to.
Issue access tokens to facilitate programmatic access to, and the ability to decrypt, edit, and create secrets.
To add a machine account for this project:
Use the New dropdown to select Machine account:

New machine account Enter a Machine account name and select Save.
Open the machine account and, in the Projects tab, type or select the name of the project(s) that this machine account should be able to access. For each added project, select a level of Permissions:
Can read: Machine account can retrieve secrets from assigned projects.
Can read, write: Machine account can retrieve and edit secrets from assigned projects, as well as create new secrets in assigned projects or create new projects.
Access tokens facilitate programmatic access to, and the ability to decrypt and edit, secrets stored in your vault. Access tokens are issued to a particular machine account, and will give any machine that they're applied to the ability to access only the secrets associated with that machine account. To create an access token:
Select Machine accounts from the navigation.
Select the machine account to create an access token for, and open the Access tokens tab:

Create access token Select the Create access token button.
On the Create Access Token panel, provide:
A Name for the token.
When the token Expires. By default, Never.
Select the Create access token button when you're finished configuring the token.
A window will appear printing your access token to the screen. Copy your token to somewhere safe before closing this window, as your token cannot be retrieved later:

Access token example
This access token is the authentication vehicle through which you'll be able to script secret injection to your machines and applications.
Now that you've got the hang of creating the infrastructure for securely managing secrets, and of creating pathways for machine access to secrets, let's continue on to the Developer Quick Start guide.