SAML 2.0 Configuration
Users who authenticate their identity using SSO will be required to enter an SSO identifier that indicates the organization (and therefore, the SSO integration) to authenticate against. To set a unique SSO Identifier:
Log in to the Bitwarden web app and open the Admin Console using the product switcher ():
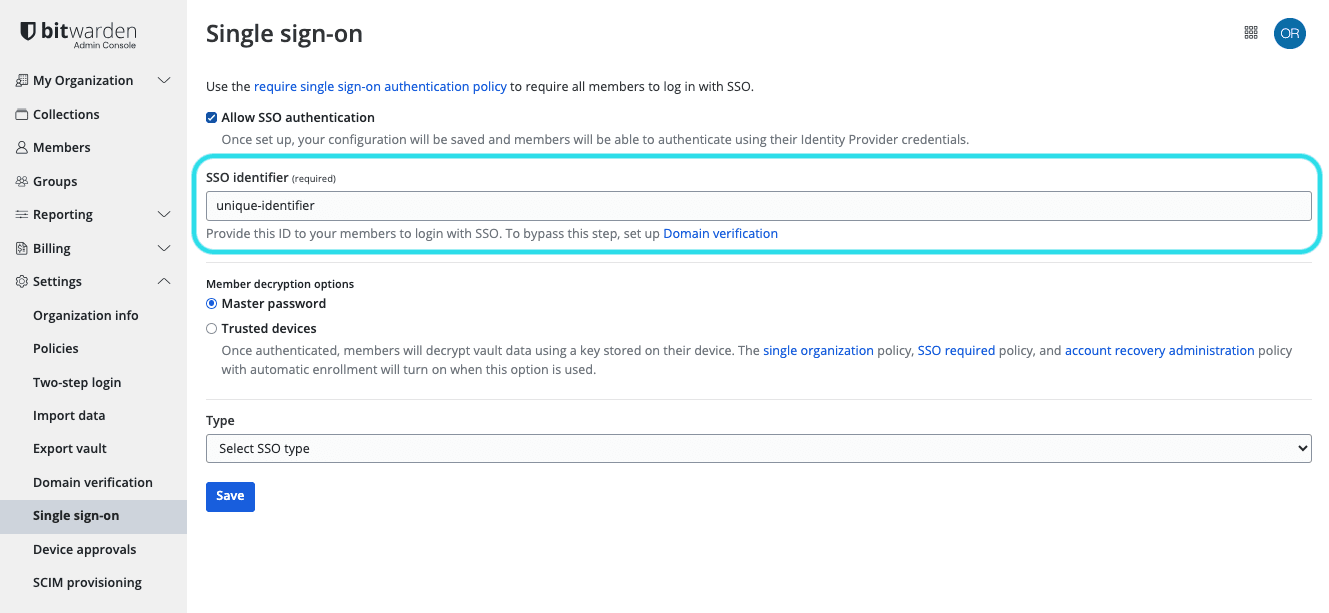
Product switcher Navigate to Settings → Single sign-on, and enter a unique SSO Identifier for your organization:
Enter an identifier Proceed to Step 2: Enable login with SSO.
tip
You will need to share this value with users once the configuration is ready to be used.
Once you have your SSO identifier, you can proceed to enabling and configuring your integration. To enable login with SSO:
On the Settings → Single sign-on view, check the Allow SSO authentication checkbox:
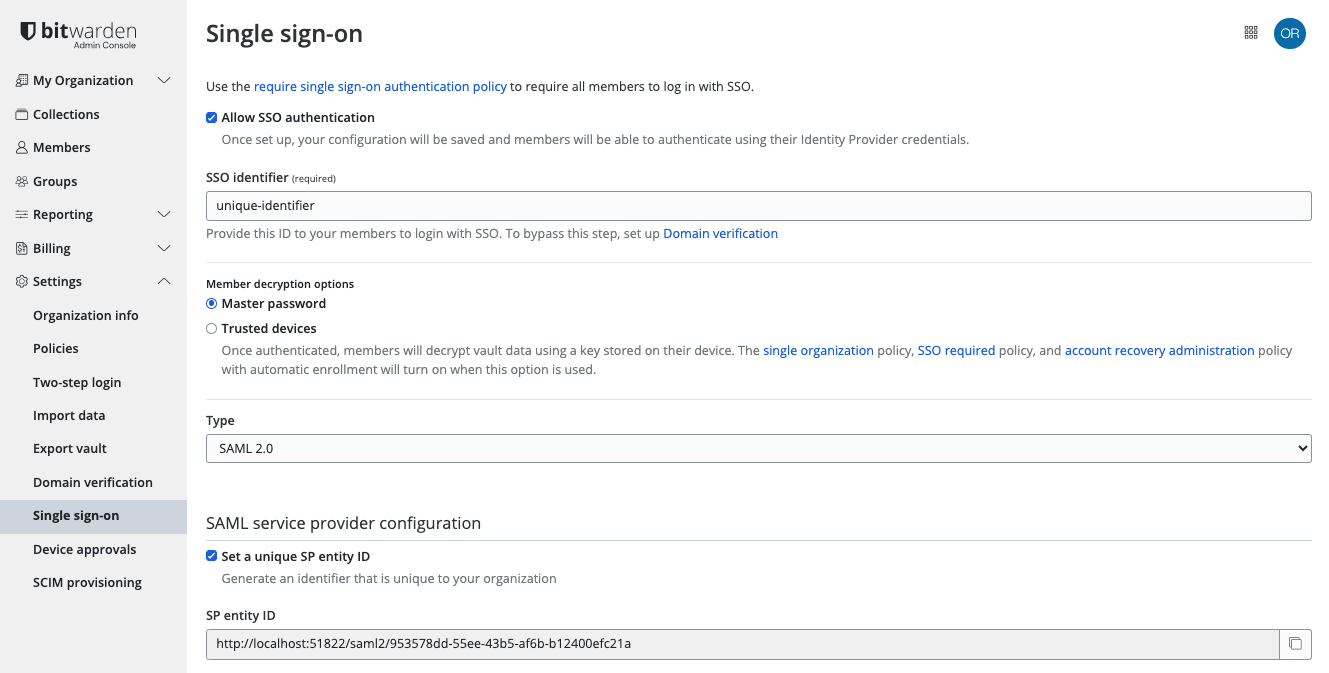
SAML 2.0 configuration From the Type dropdown menu, select the SAML 2.0 option. If you intend to use OIDC instead, switch over to the OIDC Configuration Guide.
You can turn off the Set a unique SP entity ID option at this stage if you wish. Doing so will remove your organization ID from your SP entity ID value, however in almost all cases it is recommended to leave this option on.
tip
There are alternative Member decryption options. Learn how to get started using SSO with trusted devices or Key Connector.
From this point on, implementation will vary provider-to-provider. Jump to one of our specific implementation guides for help completing the configuration process:
Provider | Guide |
|---|---|
AD FS | |
Auth0 | |
AWS | |
Azure | |
Duo | |
JumpCloud | |
Keycloak | |
Okta | |
OneLogin | |
PingFederate |
The following sections will define fields available during single sign-on configuration, agnostic of which IdP you are integration with. Fields that must be configured will be marked (required).
tip
Unless you are comfortable with SAML 2.0, we recommend using one of the above implementation guides instead of the following generic material.
The single sign-on screen separates configuration into two sections:
SAML Service Provider Configuration will determine the format of SAML requests.
SAML Identity Provider Configuration will determine the format to expect for SAML responses.
Service Provider Configuration
Field | Description |
|---|---|
SP Entity ID | (Automatically generated) The Bitwarden endpoint for authentication requests. This automatically-generated value can be copied from the organization's Settings → Single sign-on screen and will vary based on your setup. |
SAML 2.0 Metadata URL | (Automatically generated) Metadata URL for the Bitwarden endpoint. This automatically-generated value can be copied from the organization's Settings → Single sign-on screen and will vary based on your setup. |
Assertion Consumer Service (ACS) URL | (Automatically generated) Location where the SAML assertion is sent from the IdP. This automatically-generated value can be copied from the organization's Settings → Single sign-on screen and will vary based on your setup. |
Name ID Format | Format Bitwarden will request of the SAML assertion. Must be cast as a string. Options include: |
Outbound Signing Algorithm | The algorithm Bitwarden will use to sign SAML requests. Options include: |
Signing Behavior | Whether/when SAML requests will be signed. Options include: |
Minimum Incoming Signing Algorithm | Minimum strength of the algorithm that Bitwarden will accept in SAML responses. |
Expect signed assertations | Check this checkbox if Bitwarden should expect responses from the IdP to be signed. |
Validate certificates | Check this box when using trusted and valid certificates from your IdP through a trusted CA. Self-signed certificates may fail unless proper trust chains are configured within the Bitwarden login with SSO docker image. |
Identity Provider Configuration
Field | Description |
|---|---|
Entity ID | (Required) Address or URL of your identity server or the IdP Entity ID. This field is case sensitive and must match the IdP value exactly. |
Binding Type | Method used by the IdP to respond to Bitwarden SAML requests. Options include: |
Single Sign On Service URL | (Required if Entity ID is not a URL) SSO URL issued by your IdP. |
Single log out service URL | Login with SSO currently does not support SLO. This option is planned for future use, however we strongly recommend pre-configuring this field. |
X509 Public Certificate | (Required) The X.509 Base-64 encoded certificate body. Do not include the
and
lines or portions of the CER/PEM formatted certificate. |
Outbound Signing Algorithm | The algorithm your IdP will use to sign SAML responses/assertions. Options include: |
Allow outbound logout requests | Login with SSO currently does not support SLO. This option is planned for future use, however we strongly recommend pre-configuring this field. |
Sign authentication requests | Check this checkbox if your IdP should expect SAML requests from Bitwarden to be signed. |
note
When completing the X509 certificate, take note of the expiration date. Certificates will have to be renewed in order to prevent any disruptions in service to SSO end users. If a certificate has expired, Admin and Owner accounts will always be able to log in with email address and master password.
SAML attributes & claims
An email address is required for account provisioning, which can be passed as any of the attributes or claims in the following table.
A unique user identifier is also highly recommended. If absent, email will be used in its place to link the user.
Attributes/claims are listed in order of preference for matching, including fallbacks where applicable:
Value | Claim/Attribute | Fallback claim/attribute |
|---|---|---|
Unique ID | NameID (when not transient) | |
Email | Preferred_Username | |
Name | Name | First Name + “ “ + Last Name (see below) |
First Name | urn:oid:2.5.4.42 | |
Last Name | urn:oid:2.5.4.4 |