- Blog
- How to securely store your Secrets Manager access tokens with Bash scripting
Bitwarden Secrets Manager and developers are a match made in security heaven — empowering fast moving development and DevOps teams to securely store, manage, and automate sensitive secrets required for deploying software. Programmatic machine access to these sensitive secrets is facilitated via access tokens — granting machines within your ecosystem the ability to decrypt, edit, and create secrets. When developers store these access tokens in unsecured locations, however, they can be leveraged by bad actors attempting to steal sensitive data and access to your business environments.
This guide will demonstrate how to securely store Bitwarden Secrets Manager access tokens and automate the session authentication process with Bash scripting in Linux desktop and MacOS environments.
Set up Bitwarden Secrets Manager
Before saving an access token with macOS keychain or Linux desktop, let’s configure Secrets Manager with a secret, project, and service account.
To start, open the Bitwarden Secrets Manager web app and create a new project. Projects are the primary way of grouping secrets and assigning access later. Choose a name for the project. For this demonstration, name the project Profile.
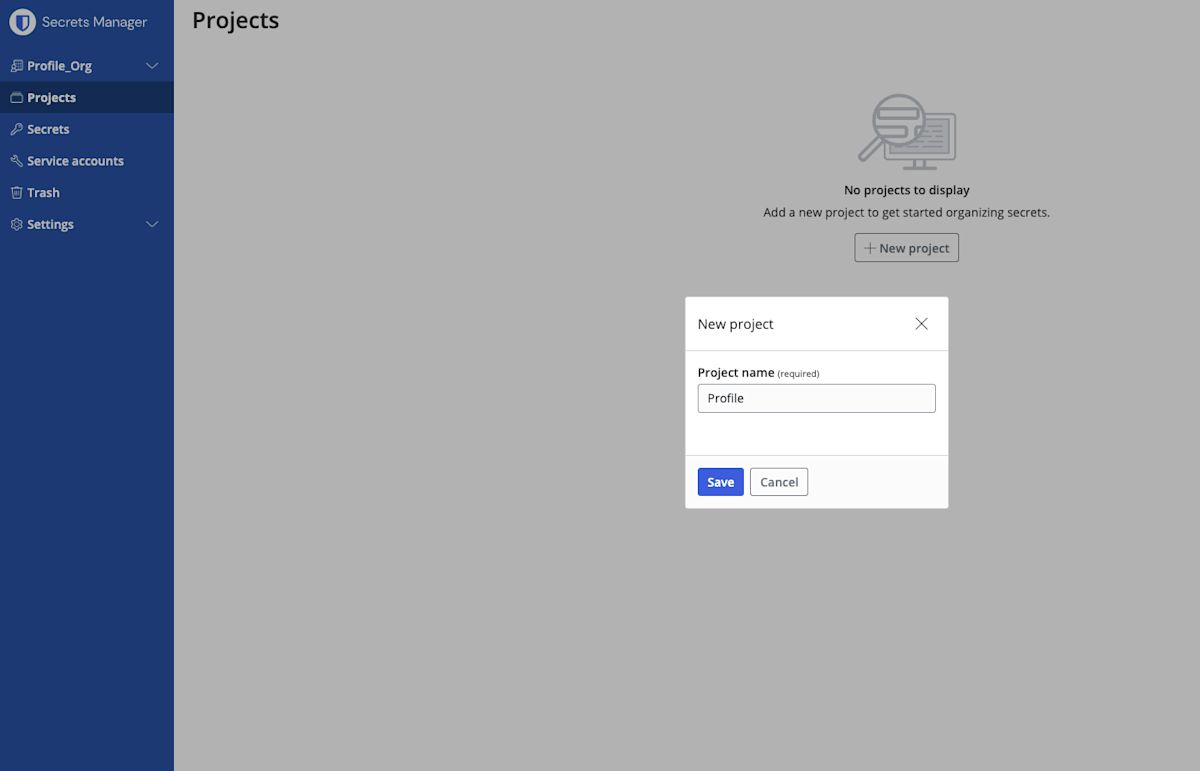
Next, create a service account. A service account represents non-human machine users that require access to a specific set of secrets. Name the service account CLI ACCESS.
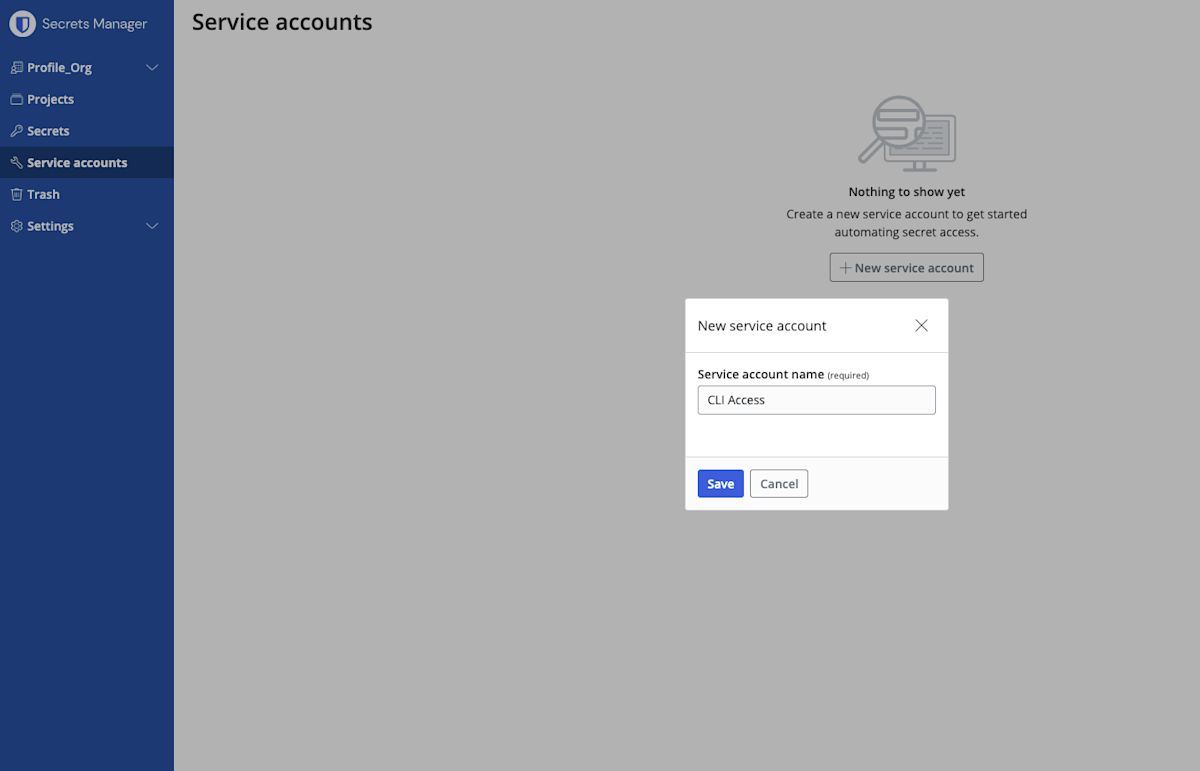
Add the service account you just created to the existing project by navigating to the project and selecting the service accounts tab. The service account should have read, write access so that the administrator's Bash profile can properly access it.
From within your service account, generate a new access token by selecting the Access tokens tab. Give the access token a name, set expiration settings, and click New access token. Remember to copy the access token value for later and save it in a safe location; it cannot be retrieved again.
Set up the Secrets Manager Command Line
Before you can securely store your access token with MacOs Keychain and Linux desktop for Bash scripting, you must first download the Bitwarden Secrets Manager CLI.
Download the Secrets Manager CLI client from GitHub and install the package on your machine. You can learn more about the Secrets Manager CLI in this help article.
Storing access tokens with MacOS Keychain
MacOS Keychain is an encrypted container for securely storing various types of confidential information, including Bitwarden Secrets Manager access tokens. More information on macOS Keychain can be found in Apple’s user documentation.
Create a Keychain item
Have the access token that was created in Secrets Manager on hand when following these steps.
Open Keychain on your system and create a new Keychain item.
Name the item BWS_ACCESS_TOKEN.
In the Account Name field, enter the account you are using on your system. This will determine access to the key and the password required to use the key.
In the password field, input the access token that was previously created in the Secrets Manager GUI.
Once you are finished, select Add.
Inject access token into Bash script
Now return to the terminal and open .bash_profile. Insert your access token securely into the .bash_profile script.
Bashexport BWS_ACCESS_TOKEN="$(security find-generic-password -w -s 'BWS_ACCESS_TOKEN' -a "<Account Name>")"Save and exit the text editor. Next, source the updated Bash profile to apply changes.
Bashsource .bash_profile
Now that the access token is set to an environment variable in your Bash profile, input your macOS user password to establish access to Bitwarden Secrets Manager.
Test that the connection works by running the following command.
Bashbws project listThe project created during the earlier step should be returned as a JSON object in your terminal.
Storing access tokens with Linux desktop
Bitwarden Secrets Manager access tokens can also be securely stored with Bash scripting in Linux desktop environments using the GNOME keyring and libsecret-tool. Please note that this method does not work in a headless environment.
Install GNOME Keyring, libsecret-tool and DBUS
The applications GNOME Keyring, lib secrets, and DBUS will be used to securely store the access token. GNOME Keyring is a software application integrated with the user’s login, allowing secrets, passwords, and keys to be made available for application access. GNOME Keyring will be used in conjunction with Libsecret, a library for securely storing and retrieving passwords and secrets. The application DBUS will help libsecret communicate with GNOME Keyring. Use the commands below to install these applications.
Bashsudo apt-get update
Bashsudo apt-get install -y gnome-keyring libsecret-tools dbusx11
Inject access token into Bash script
The following command will store the access token with libsecret and GNOME Keyring:
Bashsecret-tool store –label=”<label>” “<attribute>” “<value>”
When storing a secret with secret-tool, a label argument is required. This argument will be displayed in the secret-tool manager. For each secret stored, a unique attribute and value are required.
Here is an example of the populated command.
Bashsecret-tool store –label=”auth” “BWS_ACCESS” “TOKEN”
After entering the above command, the terminal will prompt you to submit a password on a single line. Enter the access token created previously in the Secrets Manager GUI and press enter.
A GUI popup will appear and ask for the access password to this key. Here you will set your preferred password to call this key in the future.
Check that the key was saved by entering the following command.
Bashsudo secret-tool lookup “<BWS_ACCESS>” “<TOKEN>”
If the lookup returned your stored password, the key storage was successful. Next, open the .bash_profile where you wish to save the environment variable.
Save the following function in your script to lookup the BWS_ACCESS_TOKEN that was saved and run the function as an environment variable.
Bash$ export BWS_ACCESS_TOKEN=”$(secret-tool lookup “<BWS_ACCESS>” “<TOKEN>”)”Save the changes and run the .bash_profile script in your terminal.
Bashsource .bash_profile
You will be prompted to enter the password you just set to secure your key. Once you have entered the password, test that the environment variable was properly created by running the following command.
Bashbws project listThe project created during the earlier step should be returned as a JSON object in your terminal. If the key storage was unsuccessful, or you would like to learn more about libsecret-tool, see the Ubuntu documentation.
Start securing your developer pipeline with Bitwarden Secrets Manager
With Bitwarden Secrets Manager, developers have the tools they need to secure critical infrastructure secrets. See it in action and sign up for free or start a 7-day business trial.