Using Bitwarden Secrets Manager and GitHub Actions to upload to an app marketplace
- Blog
- Using Bitwarden Secrets Manager and GitHub Actions to upload to an app marketplace
Bitwarden Secrets Manager empowers development, DevOps, and cybersecurity teams to securely store, manage, and deploy critical secrets within software development workflows. Leverage the GitHub Actions integration to streamline and automate these pipelines — ensuring strong security against bad actors.
The following article explores how to use Bitwarden Secrets Manager and GitHub Actions to securely inject secrets into a GitHub workflow and upload an application to a marketplace.
In this walkthrough, we will be using the Bitwarden Secrets Manager GitHub Actions integration to encrypt and authenticate updates to a “Hello World” project repository. This repository manages the hw-docker image for an application. By using Bitwarden Secrets Manager and GitHub Actions together, you can streamline the build process for the Docker image.
To start, let's open the Bitwarden Secrets Manager web app. Tip: make sure to navigate to Secrets Manager in the top right if you are logging in for the first time.
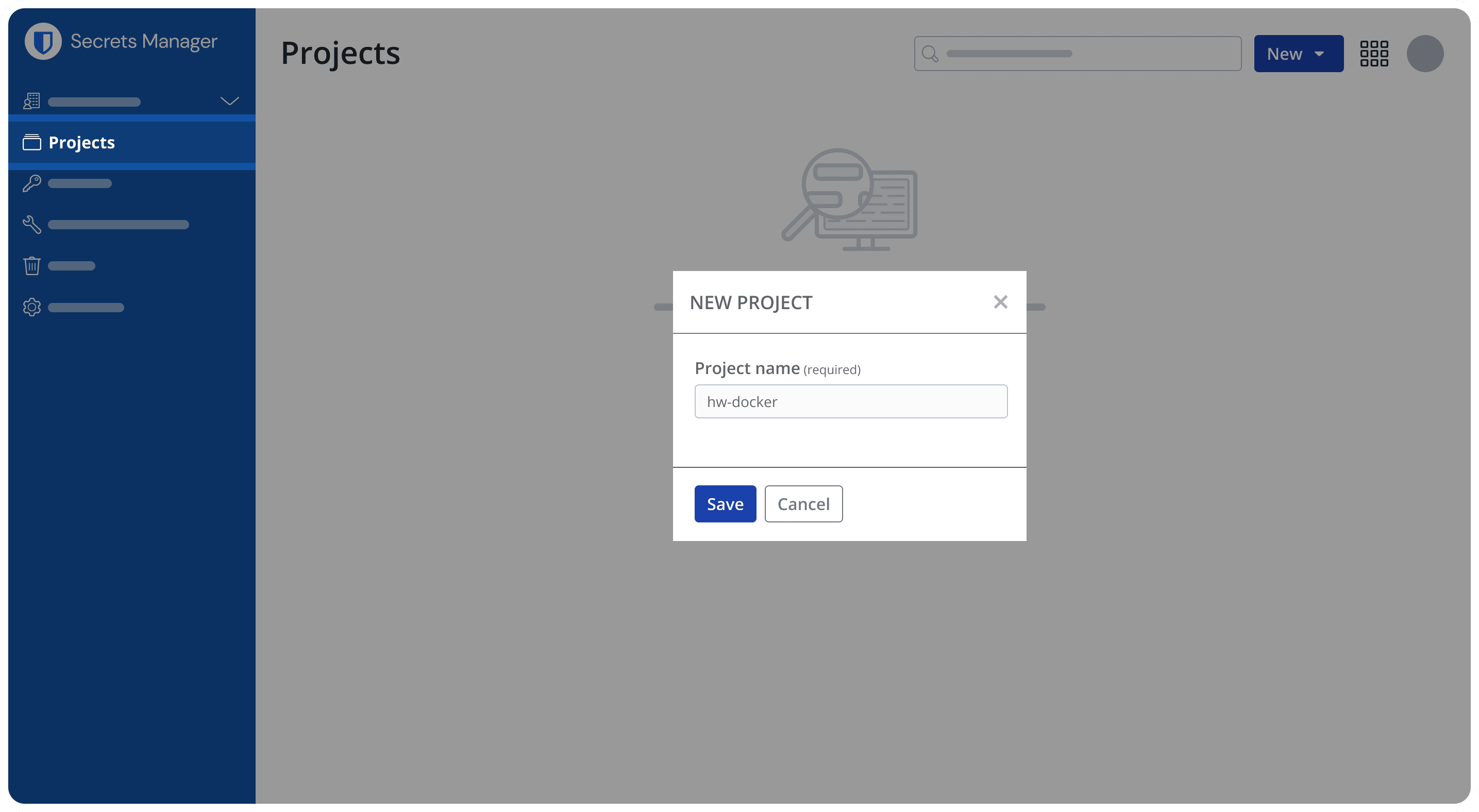
From the Secrets Manager web app, create a new project. Projects are the primary way of grouping secrets and assigning access later. Here we will be naming the project after the ‘hw-docker’ Docker image, to represent the Hello World project.
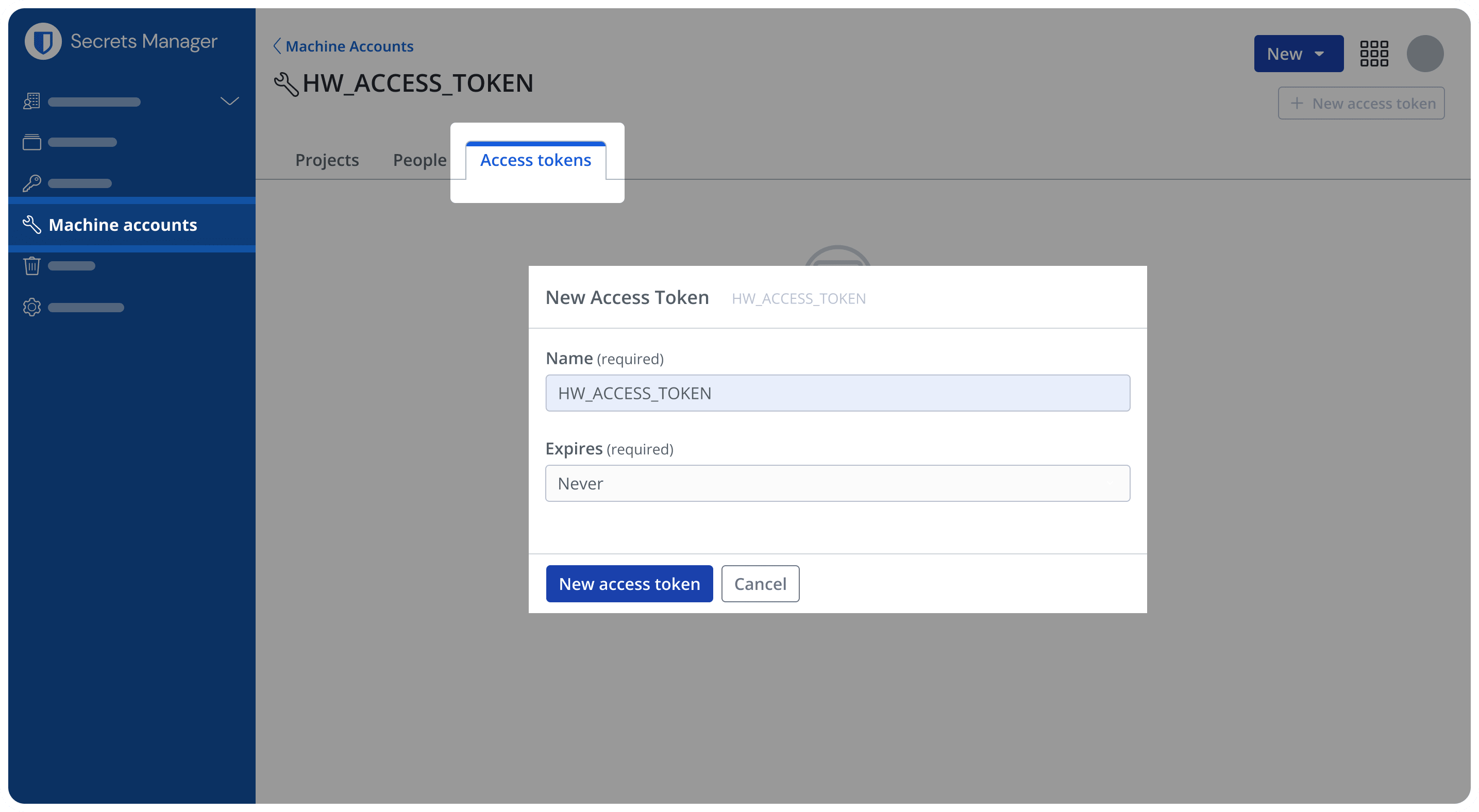
Next, create a machine account. A machine account represents non-human machine users that need access to a specific set of secrets. This machine account will enable GitHub Actions to perform its workflow in the repository via an issued access token. Let's name the machine account HW_ACCESS_TOKEN to represent this.

After you create the machine account, add it to your project by navigating to the project and selecting the Machine accounts tab. You can choose if you would like the machine account to have read or read, write access. For this project, we recommend selecting read access because GitHub Actions does not need to edit the secrets to perform the workflow.
This access token will be used to securely store it as a GitHub encrypted secret.
From within your machine account, create the access token and give it a name.
Make sure to copy and save this value in a safe location; it cannot be retrieved again.
With your access token copied, go to GitHub and navigate to your repository. Select the Settings tab and navigate to Secrets and variables, then Actions on the side bar.
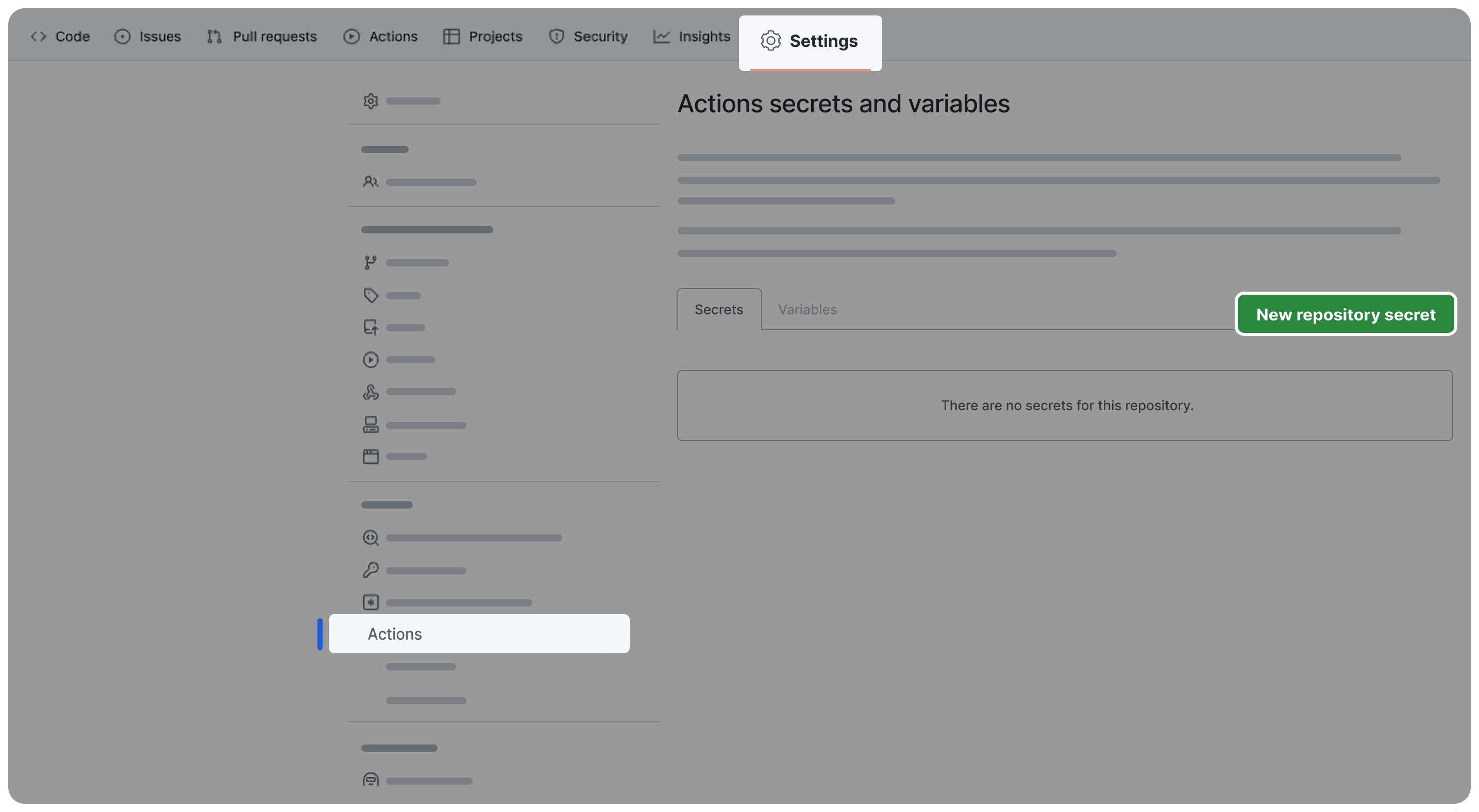
Create a new repository secret — we recommend giving your secret the same name as the Bitwarden access token (HW_ACCESS_TOKEN). Paste the access token value into the secret input and select Add secret once you have finished. Now that the access token is stored in GitHub as a repository secret, the access token can be securely inserted into the Actions workflow file.
HW_ACCESS_TOKEN is the variable name that GitHub action will use for authenticating with Bitwarden Secrets Manager.
The Bitwarden Secrets Manager CLI is how we will be retrieving and injecting your secrets.
Download the Secrets Manager CLI. If you are using a Linux machine, the following commands can also be used to download in the terminal:
curl -LO https://github.com/bitwarden/sdk/releases/download/bws-v0.2.1/bws-x86_64-unknown-linux-gnu-0.2.1.zip
unzip <~/dir/>
sudo mv bws /usr/local/binOnce the Secrets Manager CLI has been installed, check the status by entering:
bws --versionor
bws --helpFor more details on using the Secrets Manager CLI, see the Bitwarden documentation.
Now that Secrets Manager CLI has been installed, it's time to authorize your session. This will be done with a new machine account and new access token. Create a new machine account called BWS_ACCESS_TOKEN. Assign this machine account to the project, in this case hw_docker with read or read, write access. We recommend choosing read, write access in case you decide to edit or add new secrets from the CLI.
Now, create a new access token on the newly created machine account. Use the new access token to authorize the CLI session in the terminal by entering:
export BWS_ACCESS_TOKEN=<token value>To build and run the Docker image, you’ll need to set up the GitHub Actions workflow. Having Quickstart for GitHub Actions quide open and available for this part may help!
Create a .github/workflows directory in your repository if you do not already have one. In this dir, create a YAML file and name it docker-image.yml — designating this file as being used to build the docker image.
The first section of the file will be as follows:
name: Push to Docker Hub
on:
workflow_dispatch:
inputs:
version:
description: "hello world version (just the numbers, e.g. 2023.1.0)
required: true
type stringIf you need any additional information on the fields, GitHub's documentation does an excellent job explaining the core components of the file.
The next section of the file will be the actions and workflows that will run when initiating the workflow on GitHub:
jobs:
build:
runs-on: ubuntu-latest
steps:
- name: Bitwarden Secrets Manager GitHub Action
uses: bitwarden/sm-action@v1.0.0
with:
access_token: ${{ secrets.HWS_ACCESS_TOKEN }}
secrets: |
00000000-0000-0000-0000-000000000000 > DOCKER_USER
00000000-0000-0000-0000-000000000000 > DOCKER_PAT
- uses: actions/checkout@v3
- name: docker login
run: docker login -u $DOCKER_USER -p $DOCKER_PAT
- name: docker build
run: |
docker build . --file Dockerfile --tag $DOCKER_USER/"hwdocker":latest \
--tag $DOCKER_USER/"hwdocker":${{ github.event.inputs.version }} \
--tag $DOCKER_USER/"hwdocker":v${{ github.event.inputs.version }}
- name: docker push
run: docker push -a $DOCKER_USER/"hwdocker"
DOCKER_PATwill be the personal access token for Docker, saved as a Secrets Manager secret.
This workflow will use the Bitwarden Secrets Manager GitHub Action to inject authentication and Checkout V3 to run the code against the existing repository.
actions/checkout@v3 will checkout your action onto the runner, allowing you to run scripts or other actions against your code.
Next, create the following secrets in Bitwarden Secrets Manager to securely inject within the workflow.
DOCKER_USERis the Docker username that you use in order to access your Docker account that manages the image we are going to update.DOCKER_PATis the access token that is used in place of a traditional password to access your Docker Hub account.
This step can also be done from the CLI, see the Secrets Manager CLI for details.
To create these secrets, navigate to the Secrets Manager web app and head to the Secrets tab. Create a new secret for DOCKER_USER and DOCKER_PAT. We suggest keeping the Key the same as the intended name. Input the value for each into the value category.
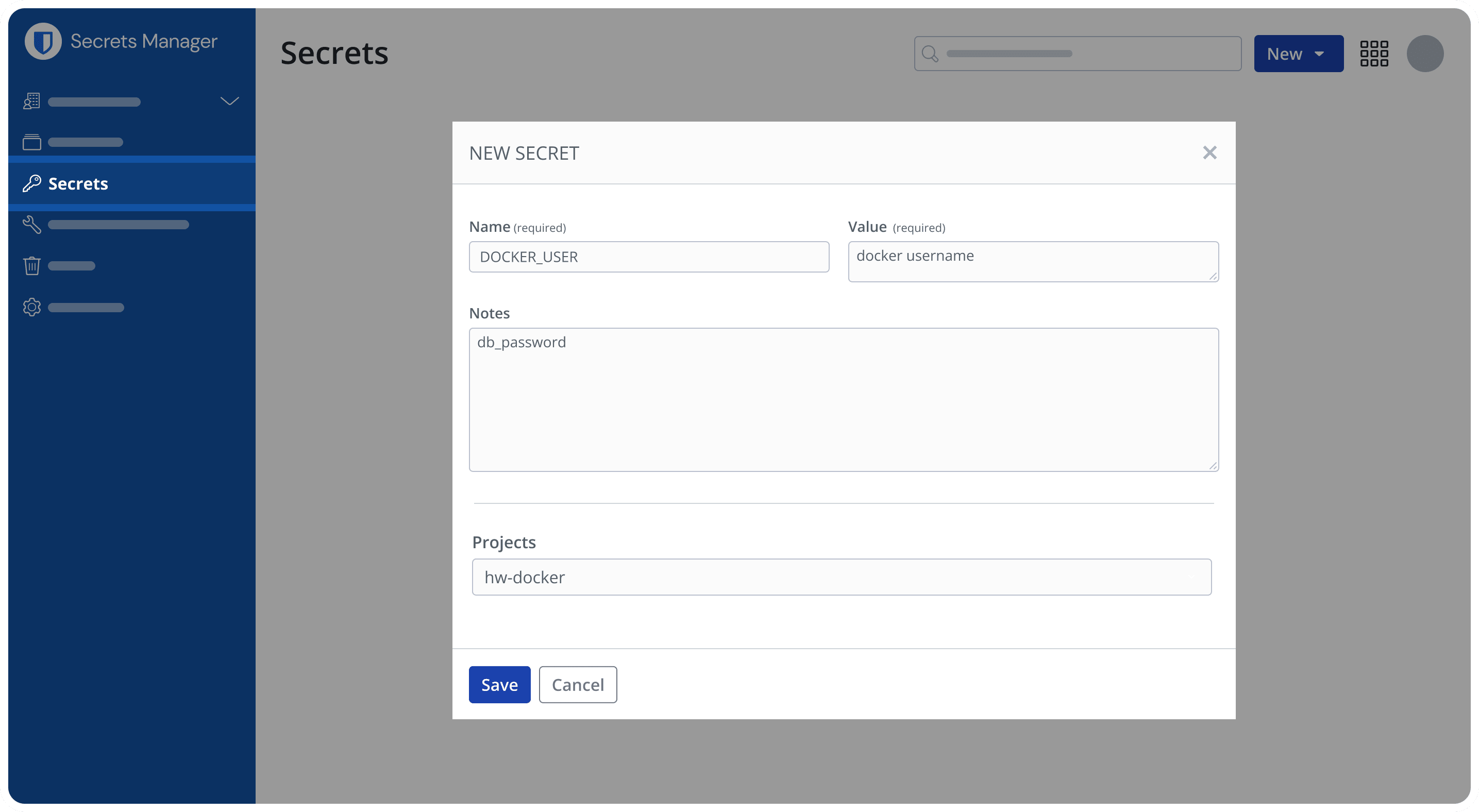
Tip: be careful to avoid trailing whitespace while entering the secret value.
Inserting the DOCKER_USER and DOCKER_PAT secrets into `docker-image.yml` will maintain end-to-end encryption of those secrets when we place them in the appropriate fields.
The secrets must then be assigned to the project we are working on. In this case, hw-docker. Once the secrets are saved and assigned to the project, retrieve your secret ids in the terminal by entering:
bws secret listThe output will provide a list of secret objects that your machine account has access to. For example:
{
"object": "secret",
"id": "00000000-0000-0000-0000-000000000000",
"organizationId": "00000000-0000-0000-0000-000000000000",
"projectId": "00000000-0000-0000-0000-000000000000",
"key": "DOCKER_USER",
"value": "docker username",
"note": "",
"creationDate": "2023-07-20T21:30:09.2810007Z",
"revisionDate": "2023-07-20T21:30:09.2810007Z"
}The values for id is what we are looking for. Insert the two secret ids into the following section:
secrets: | 00000000-0000-0000-0000-000000000000 > DOCKER_USER 00000000-0000-0000-0000-000000000000 > DOCKER_PAT
Next insert the value for the access token:
Bashaccess_token: ${{ secrets.HWS_ACCESS_TOKEN }}Do not enter the actual access token value.
For this example we will also need a very simple Docker file to maintain the Docker image.
FROM alpine
CMD ["echo". "Hello World"]Now that the setup for the workflow file is complete, test if the workflow is successful. On your terminal, head to the actions tab and manually engage a workflow. There will be an option on the left-side menu to select the workflow; in this case it is Push to Docker Hub. Click the Action and then select Run workflow.
After the workflow has been started, the system will run through the job and provide a status report of success or failure. In the report you can review the job and details on what was successful — and what might not have been. In the screenshot below, all job actions were successfully completed.

As developers, you want to manage secure information with ease, without compromising security. With the Bitwarden Secrets Manager GitHub Actions integration, inject secrets into a GitHub workflow to securely build a Docker image, while protecting critical secrets with end-to-end encryption. By incorporating Secrets Manager to your team’s GitHub Actions workflow, you can manage encrypted authentication and uphold CI/CD.
This example illustrates how Bitwarden Secrets Manager empowers development teams to securely streamline their day-to-day operations and processes.
Bitwarden is trusted by millions of individuals and businesses across the globe to secure sensitive information and credentials. Get started securely automating your critical secrets into developer workflows and sign up for Bitwarden Secrets Manager!
Editors note: This article was originally published on August 30th, 2023, and was updated on April 2nd, 2024 to reflect “machine accounts”, originally called “service accounts”. This name update provides enhanced clarity on the feature’s function, which is the facilitation of machine interactions with secrets stored in Bitwarden Secrets Manager.