Basics of two-factor authentication with Bitwarden
- What is two-factor authentication (2FA)?
- How does it work
- Recovery Codes
- Common two-step login mechanisms
- Text message
- Authenticator Application
- Hardware Keys
- How does Bitwarden use two-step login
- Using two-step login for your Bitwarden vault
- Using the Bitwarden Authenticator with external accounts
- Two-step to go
- Blog
- Basics of two-factor authentication with Bitwarden
Catch our webcast replay covering this topic.
View the presentation from the webcast.
Using two-factor authentication helps increase user security for websites and applications. The name refers to requiring users to utilize two separate methods of verifying their identity in order to access an account. A common definition for 2FA is that logging into a service involves something that you know, such as a password, and something that you have, such as your phone, hardware token, or other authentication code.
A common example is when you log into a website with a username and password, and then receive a text message code for a final validation of your access. The username/password is the first factor, and the text message code received on your phone is the second factor — hence, two factor authentication.
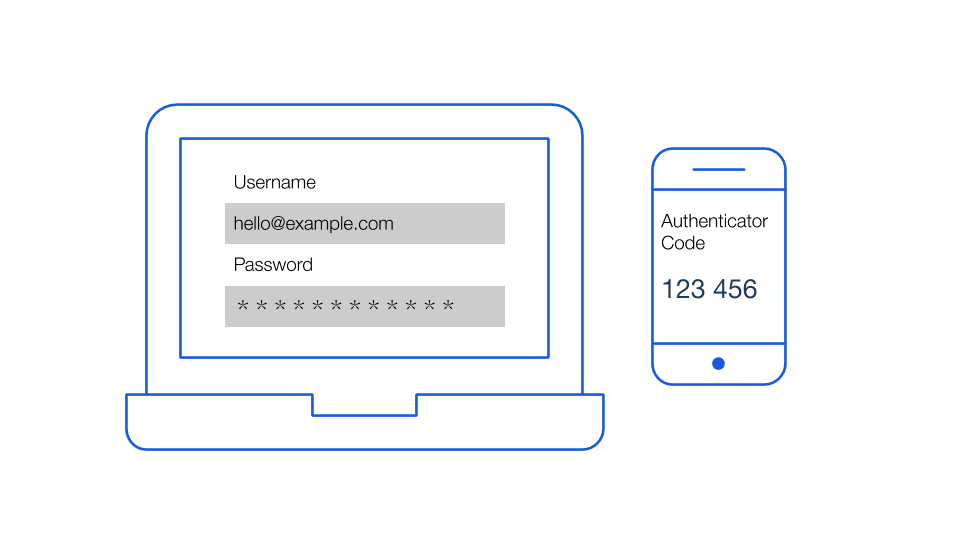
Bitwarden refers to this process as two-step login, which is another term for two-factor authentication that is more consumer friendly. Other terms include multi-factor authentication and two-step verification. All of these terms imply a secondary step in the login process to verify your identity.
Two-step login can be set up when you establish an online account, or after your account is in place. Typically it involves adding a second layer of login security to a username and password combination.
Here’s an example of the same process as explained on the Amazon website. They use the term two-step verification.
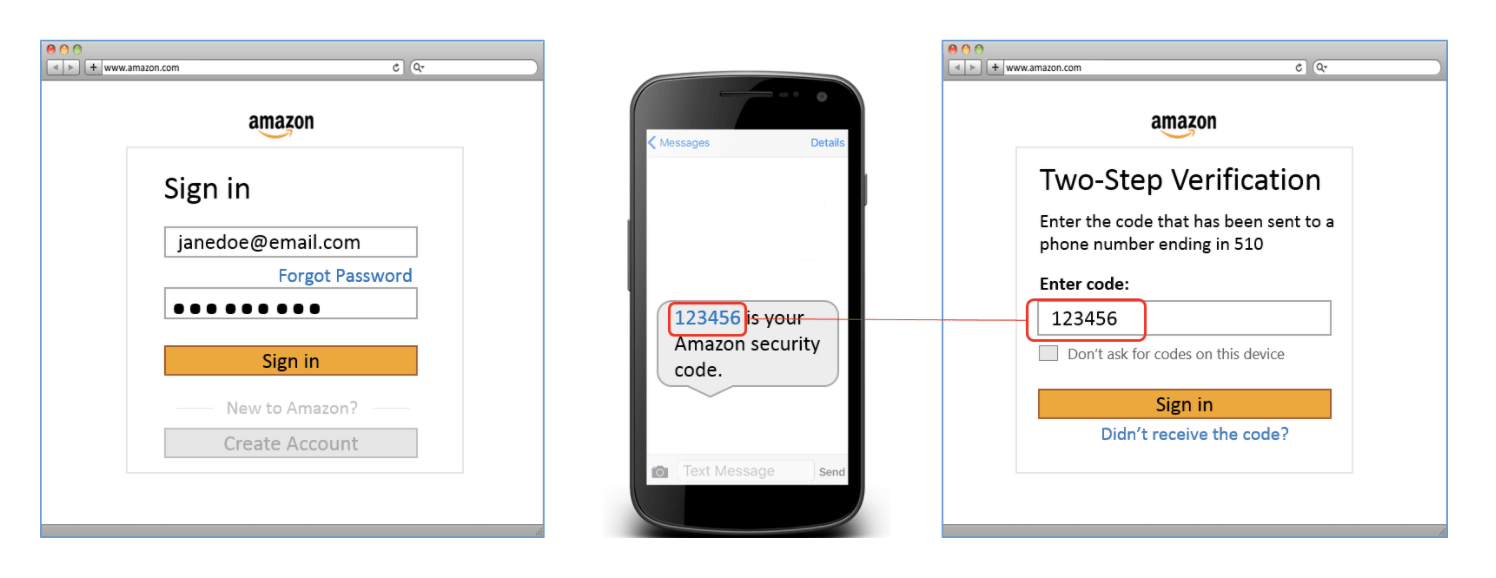
The general thinking is that while it might be possible for someone to gain access to your email and password, the likelihood of that bad actor also having your mobile phone is significantly less.
Most websites offering two-step login will provide Recovery Codes should you ever lose your ability to provide the second step. Recovery Codes are important and should be treated with care, as well as kept in a secure and memorable place. Some people like to retain Recovery Codes digitally, others keep a printed copy, some both.
With many services (including Bitwarden) if you ever lose access to your 2FA device, the only way to recover the account is with the recovery codes. Without the recovery codes you can get locked out of the account forever.
Because two-step login significantly improves security, everyone benefits from being able to choose among the several alternatives that have evolved for implementing the second factor. You will often see multiple options for two-step login including:
An email sent to you with a temporary code
A text message temporary code sent to your mobile phone
A time-based code on an authenticator application
A hardware key such as a YubiKey or SoloKey
A fingerprint, facial scan, or other biometric data point
Let’s briefly discuss the benefits and risks of these various options. Spoiler alert: while authenticator applications and hardware keys tend to be the most popular among security enthusiasts, be aware that by using any of these methods, you will significantly increase the security of your authentication procedure.
Email provides basic security for two-step login. The assumption is that while someone might know your email address and user account password, they are less likely to have access to receive email at that address. So sending a code to your email address upon login provides a basic second verification step.
Text messages also provide a second complement to logging in with an email and password. The assumption is that while someone could have your email address and account password, they are far less likely to have access to your mobile phone too. So, the text message code provides the second verification step. However, phone numbers have been known to be ported without the owner’s knowledge, which makes this method less secure than others that follow.
Authenticator applications provide another level of security for two-step login, and generally use a technique called a Time-based One Time Password, or TOTP for short. These Authenticator applications are typically free for users to download to their phones or tablets from app stores, and include products like Authy, Google Authenticator, Microsoft Authenticator, FreeOTP, Aegis, Duo Security and more.
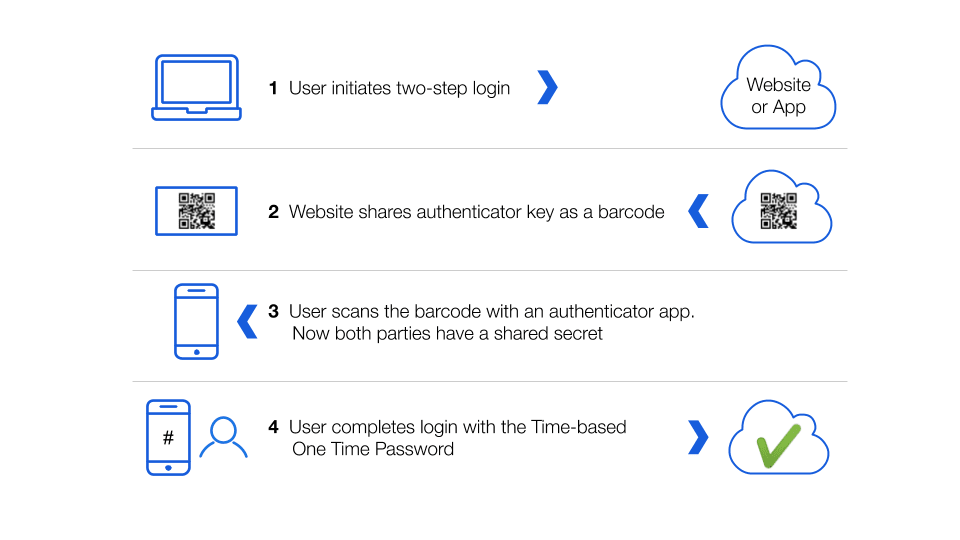
The sequence for setting up a website to use an Authenticator app for two-step login generally flows like this:
The user accesses the website or application where they want to add two-step login and initiates that setup process.
The website shares an authenticator key as a QR code. If for some reason the QR code does not work, the authenticator key is often made available as a long text string.
The user scans the QR code using their camera with the Authenticator application they downloaded to their phone or tablet. Now both the Authenticator app and the website/application that will use two-step login have a shared secret.
The user now has an Authenticator app that is enabled with the shared secret to generate Time-based One Time Passwords. These are usually 6-digit codes that last for 30 seconds. The next time the user goes to login to the website/application, it will prompt not only for username/password, but then also for the time-based 6-digit code. That code will change to a new code every 30 seconds on both the Authenticator app and within the website/application login system, thus providing more security than just receiving a verification code via email or text message.
Physical devices provide a further level of security for two-step login. By using a hardware-based key, not replicable without the key itself, users can ensure that no one else can log into their account without the same key. YubiKeys and SoloKeys are just a couple of product examples.
You can set up two-step login for accessing your Bitwarden vault itself with authenticator applications, YubiKeys, FIDO U2F security keys, Duo Security, or email. Some of these options require Bitwarden Premium Features. For more on enabling two-step login to access your Bitwarden vault visit this help note.
A few of our favorite 3rd party authenticators include Authy, Aegis, Duo Security, FreeOTP, Google, and Microsoft.
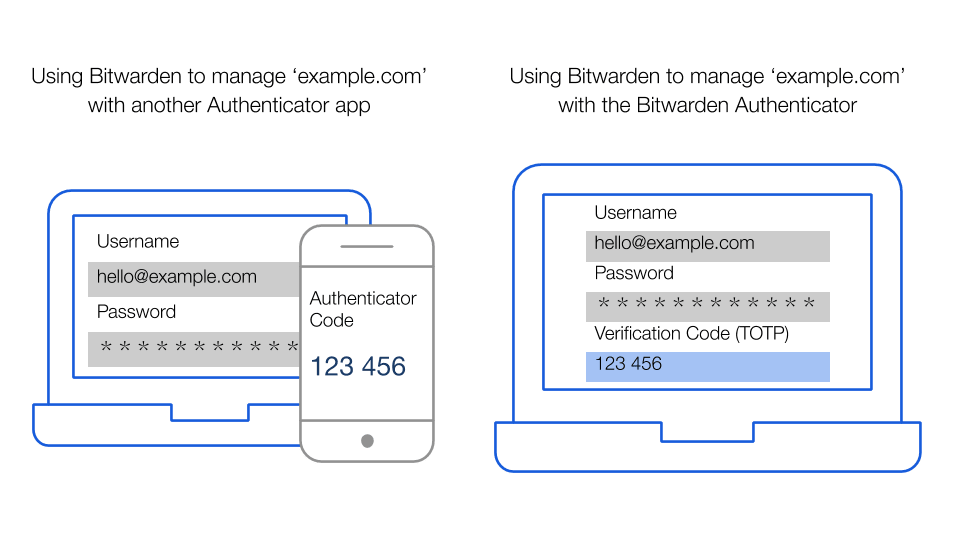
Bitwarden also allows you to manage and facilitate two-step login for individual websites and external accounts stored within your vault. This uses the Bitwarden Authenticator, built into the Bitwarden application and part of Premium Features. Using the Bitwarden Authenticator to autofill the TOTP code can be set up if the web service supports third party authentication apps such as Authy and Google among others.
Here’s how this works. When you set up two-step login within a website or application and are presented with the QR code referenced in step 2 above, you can scan it with the mobile version of Bitwarden and add it to the login information within the Bitwarden vault for that site. Alternatively, you can also add the text string format version of the authenticator key to the Bitwarden vault entry for that website/application. Then, when you use Bitwarden to login to the website/application thereafter, once you enter your username/password and are prompted for the authenticator time-based code. This code is auto-copied to your clipboard when performing autofill operations in the app. You can also retrieve the time-based authenticator code from the Bitwarden app, extension, or from the clipboard (if you’re not using password auto-fill).
NOTE: If you are using the Bitwarden Authenticator, on completion of autofill, Bitwarden will automatically copy the six digit verification code to your clipboard. You can then quickly paste it for the final login step. Note that this feature is only enabled if you do NOT select the “Enable Autofill on Page Load” option in Bitwarden Settings > Options
Of course, some may ask what is the point of having your username, email, and your two-step login code all stored within the same application — namely Bitwarden? Doesn’t that negate the value of two-step login?
The answer depends. Let’s break it down.
Your Bitwarden Vault hopefully already has two-step login using some other method. (ie. do not use the Bitwarden Authenticator to protect your Bitwarden account.) Therefore it is currently protected with a high level of security and, in fact, two-step login.
Having two-step login enabled for websites and applications is always better than not having it enabled. A tighter bundling of two-step login makes it easier to use more frequently, which promotes better security hygiene as a practice.
If you need to share an item, you can share it with two-step login enabled, which, again, is better security practice. This is a collaboration and two-step login power move.
You do not need to remember which authentication app you used, since it is built in.
You can always choose, on an individual basis, which login you want to authenticate internally within the Bitwarden app, or externally using a separate Authenticator app.
Bitwarden users find that the integrated Authenticator functionality provides faster workflows with better security and dexterity for collaboration. Users also note that they apply different policies to different types of accounts. Primary financial institutions may be authenticated externally using a separate Authenticator app, while all of their ecommerce logins are authenticated internally within Bitwarden.
In a nutshell, here’s what we recommend
Enable two-step login for your Bitwarden vault with an authenticator application or one of our other recommended options.
Learn how to use the Bitwarden Authenticator, especially in sharing and collaboration cases. Understand the ease at enabling two-step login for external accounts and the speed at which you can breeze through securely.
Pick the right mix for your own security profile. The choice is yours. We see scenarios where all external account two-step login information can be stored in Bitwarden, and others where a mix makes sense.
To get started with Bitwarden, and premium features including the Bitwarden Authenticator, visit bitwarden.com.