Securing your GitHub Account with Bitwarden
- Choosing the best protection for two-factor authentication
- Using Bitwarden to secure your GitHub account
- Adding integrated two-factor authentication with Bitwarden for GitHub
- Enable two-factor authentication in GitHub
- Use an authenticator app
- Scan the QR code
- Use the Bitwarden mobile app
- Keep your recovery codes!
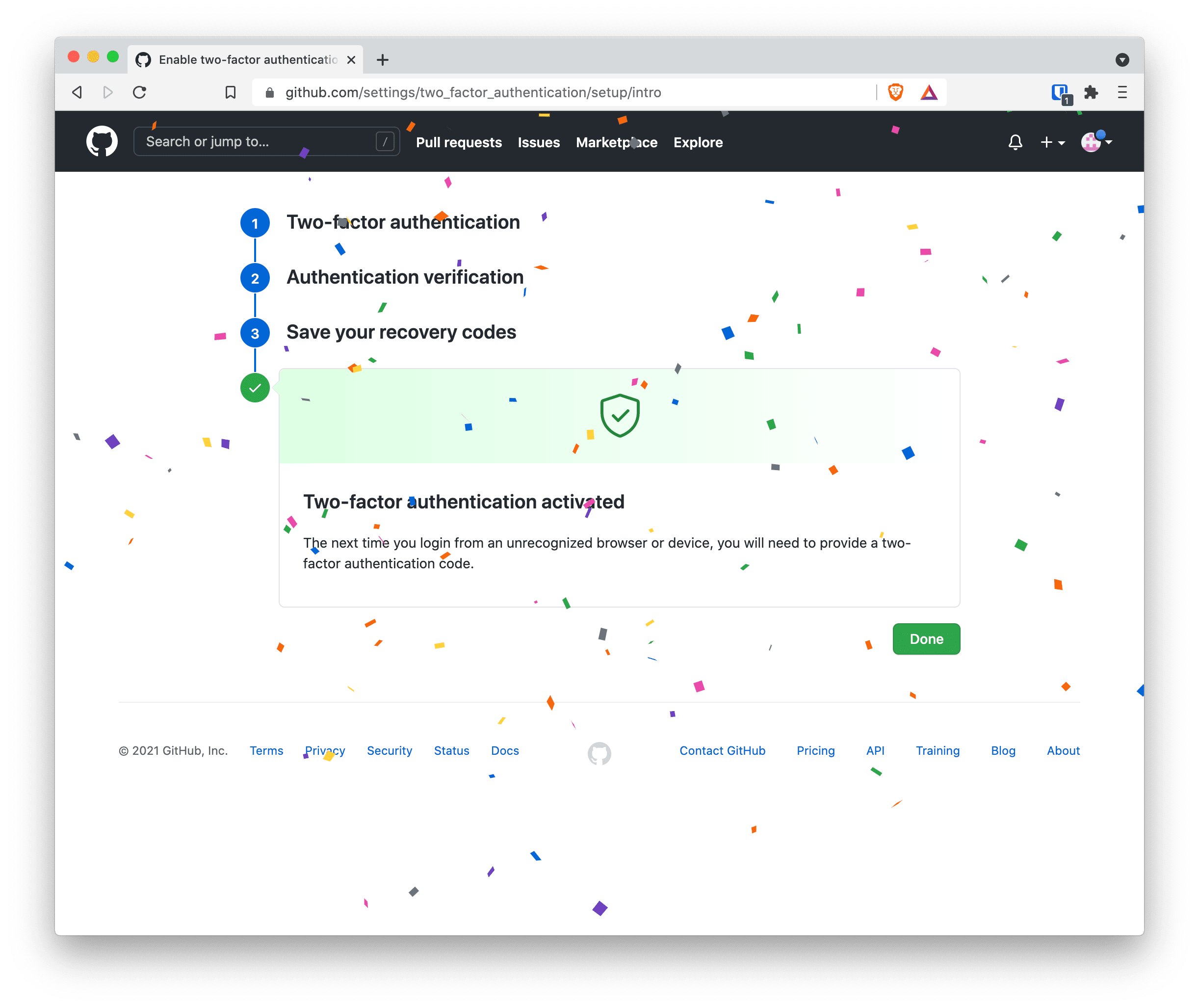
- Congratulations two-factor authentication is enabled
- Benefits of using the Bitwarden Authenticator
- Storing SSH Keys in Bitwarden for Git Authentication
- Keeping track of multiple accounts
- Get started with Bitwarden today
- Blog
- Securing your GitHub Account with Bitwarden
This week GitHub shared a post, Securing your GitHub account with two-factor authentication (2FA), that outlines steps by the company to “make it easier for developers to have strong account authentication on the platform.”
GitHub outlined 3 new security updates
No more password-based authentication for Git operations - As of August 13, 2021, GitHub will require stronger authentication such as a personal access token, SSH keys (for developers), or installation tokens for all authenticated Git operations on GitHub.com
Enabling two-factor authentication (2FA) on your GitHub account - GitHub encourages users to enable two-factor authentication for their accounts, which we will dig into specifically in this post.
Commit verification with your security key - GitHub suggests that you can “digitally sign your git commits using a GPG key stored on your security key.”
In this post we will explore options to secure your GitHub account with Bitwarden, including the option to integrate two-factor authentication using the Bitwarden Authenticator. We will also share tips on storing SSH Keys and multiple accounts in Bitwarden.
GitHub suggests multiple ways you can protect your account with 2FA
Physical security keys
Virtual security keys like Windows Hello or FaceID/TouchID
Time-based One-Time Password (TOTP) authenticator apps
Short Message Service (SMS)
It is important to note that GitHub suggests avoiding SMS and sticking with TOTPs or security keys wherever possible. This is based on recommendations from the National Institute of Standards and Technology (NIST) and widely known scenarios of SIM-jacking that make SMS less secure than other options.
When it comes to securing any online account, one of the most important things you can do is to have a password that is
Long as in 14+ characters long
Complex with a collection of letters, numbers, symbols, or words
Random with no known or discernible patterns
Unique to the website for which is it used
Together these elements of a strong password will help strengthen your account security.
Bitwarden includes a password generator to help you create such passwords for your main GitHub login or any site you frequent.
Once you have a long, complex, random, and unique password for GitHub stored in your Bitwarden account you can move on to two-factor authentication.
GitHub recommends Time-based One-Time Password (TOTP) authenticator apps as a secure method for implementing two-factor authentication with your GitHub account. Fortunately, Bitwarden has this capability included with the Bitwarden Authenticator, part of our Premium Account plan, and also included with any paid Bitwarden Organization plan such as Teams or Enterprise.
To set up integrated two-factor authentication for GitHub using Bitwarden, follow these steps
Go to Account Settings > Account Security and click the button Enable two-factor authentication

Select Set up using an app

GitHub will prompt you with a QR code to scan. You can now open your existing GitHub credential in the Bitwarden mobile app.

Open your existing GitHub credential and Edit Item. Then click the camera icon to scan the QR code presented by the GitHub website. That will automatically capture the Authenticator Key which the Bitwarden Authenticator will use to generate the Verification Code (TOTP).
Enter the 6-digit Verification Code into the GitHub website.

As with any setup of two-factor authentication, keeping your recovery codes safe ensures that if you lose your two-factor authentication, you have an alternate method to access your account.
You can keep your recovery codes within Bitwarden if you choose, for example in a Secure Note. Or upload the .txt file GitHub provides to any item as a secure attachment.

Now you can rest assured that your account has an added layer of protection.
With two-factor authentication built into Bitwarden, you can rest assured that you always have it handy and ready to go. Of course some people ask what is the point of having the two-factor authentication within Bitwarden and doesn’t this negate the value of two-factor?
We break this down in more detail in this section of a blog post titled, Basics of two-factor authentication with Bitwarden.
Your Bitwarden Vault hopefully already has two-factor authentication using some other method. (ie. do not use the Bitwarden Authenticator to protect your Bitwarden account.) Therefore it is currently protected with a high level of security and, in fact, two-factor authentication.
Having two-factor authentication enabled for websites and applications is always better than not having it enabled. A tighter bundling of two-step login makes it easier to use more frequently, which promotes better security hygiene as a practice.
If you need to share an item, you can share it with two-factor authentication enabled, which, again, is better security practice. This is a collaboration and 2FA login power move.
You do not need to remember which authentication app you used, since it is built in.
You can always choose, on an individual basis, which login you want to authenticate internally within the Bitwarden app, or externally using a separate Authenticator app.
As mentioned in the start of this post, GitHub is moving to stronger authentication for all authenticated Git operations on GitHub.com
One recommended method is using SSH keys, which Bitwarden supports in Custom Fields These fields can support the length of longer items such as RSA 4096-bit SSH keys.
If you maintain multiple GitHub accounts, you can store them within Bitwarden for easy access. Bitwarden also allows for custom uniform resource identifiers (URIs) and match detection to ensure the right credentials are submitted for the right accounts. See this help note on Using URIs.
If you are not already using a password manager, today is a great time to start! You can sign up for Bitwarden for free at bitwarden.com. To use the integrated Bitwarden authenticator, sign up for any of our paid plans.