- Blog
- Protection from ransomware: how password security best practices safeguard
The U.S. federal government periodically advises individuals and businesses to keep their data protected and remain aware of cybersecurity threats. Recently, the U.S. Joint Ransomware Task Force (JRTF), an interagency co-chaired by the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI), issued a “#StopRansomware Guide” for organizations at risk of being targeted by ransomware attacks.
Authored by CISA, the FBI, and the National Security Agency (NSA), the #StopRansomware Guide “provides guidance for all organizations to reduce the impact and likelihood of ransomware incidents and data extortion, including best practices to prepare for, prevent, and mitigate these incidents.”
The #StopRansomware Guide is a necessary response to a real threat to Americans and U.S. businesses. One only needs to look to the Palo Alto Networks Ransomware and Extortion Report and the State of Ransomware Report from Sophos (both cited below) for more evidence of the damage caused by ransomware.
Businesses interested in staving off and mitigating the damage from ransomware attacks should consider reading the guide and reviewing both reports. This blog is focused on the role of password managers and passwordless technologies in protecting credentials.
Defining ransomware and understanding its scope as malicious software
The #StopRansomware Guide defines ransomware as follows:
“Ransomware is a form of malware designed to encrypt files on a device, rendering them and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. Malicious code encrypts files, making them inaccessible without the decryption key.
Over time, malicious actors have engaged in more destructive ransomware tactics. They continue to successfully exfiltrate victim data and pressure targets to pay by threatening to release or sell stolen information on the dark web. Ransomware inflicts harm by locking users out of their computers or encrypting their data.
The application of both tactics is known as ‘double extortion.’ In some cases, malicious actors may exfiltrate data and threaten to release it as their sole form of extortion without employing ransomware. The decryption key is crucial in ransomware attacks, as it is the only way to regain access to the encrypted data.”
It goes on to state:
“These ransomware and associated data breach incidents can severely impact business processes by leaving organizations unable to access necessary data to operate and deliver mission-critical services.
The economic and reputational impacts of ransomware and data extortion have proven challenging and costly for organizations of all sizes throughout the initial disruption and, at times, extended recovery.”
This explanation captures the challenges businesses face in remaining vigilant against ransomware threats. According to the 2023 Sophos State of Ransomware Report, 66% of respondents reported their organization was affected by ransomware. For comparison, in 2020, that number was 51%.
Meanwhile, Palo Alto Networks reports that half of all ransomware incidents posted on leak sites in 2023 involved U.S. organizations, trailed by Europe, the Middle East, and Africa. The manufacturing industry was the most impacted by extortion attacks, followed by the professional and legal services industries. Interestingly, Palo Alto Networks found that harassment of individuals within an organization was a factor in 20% of ransomware cases, up from 1% in the previous year.
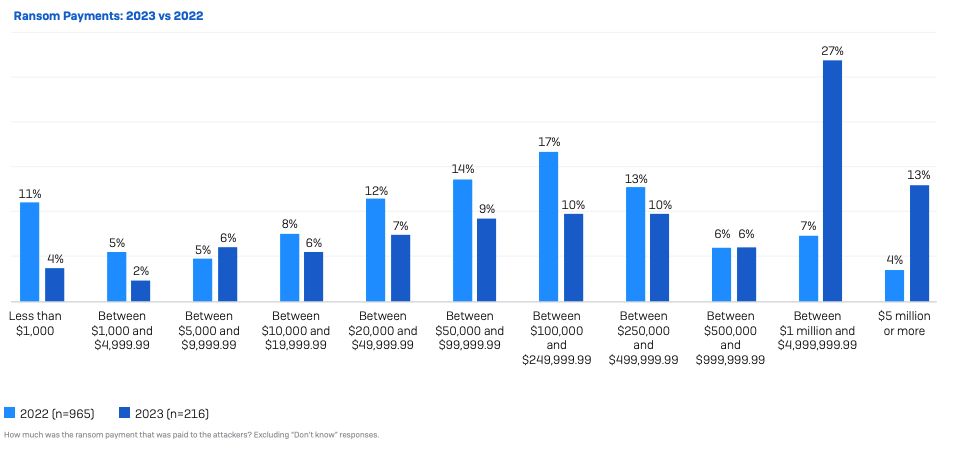
The Sophos report found that “payments themselves have increased considerably over the last year, with the average (mean) ransom payment almost doubling from $812,380 in 2022 to $1,542,333 in 2023. The median ransom payment reported in this year’s study was $400,000.” It also noted that “organizations reported an estimated mean cost to recover from ransomware attacks of $1.82 million, an increase from the 2022 figure of $1.4 million.”
The Palo Alto Networks Report also probed the financial impact of ransomware, noting ransomware payment demands ranged from $3,000 to $50 million. In actuality, payments were “as low as $3000 and as high as $7 million.” The median payment tracked by Palo Alto Networks hewed closely to the Sophos number: $350,000.
“Threat actors want you to feel pressured,” according to the Palo Alto Networks report. “The more you feel this way, the more likely you will pay what they demand. When cybercriminals use tactics such as harassment and urgency in addition to encryption, they’re trying to make you feel out of control and under pressure so you’ll do what they want.”
These figures are jarring. Fortunately, organizations can shore up security safeguards and minimize ransomware attack risks through password management best practices and passwordless authentication adoption.
Protecting credentials from ransomware attacks using security tools
While ransomware can be delivered through a number of threat vectors, the Federal Trade Commission (FTC) notes that “phishing emails make up most ransomware attacks.” As discussed in this Bitwarden blog, phishing attacks are social engineering tactics that attempt to trick people into divulging confidential information like login credentials, bank accounts, or social security numbers, or redirect victims to websites housing malware downloads. Having secure backup files offline and on the cloud is crucial to recover data more quickly in case of an attack.
Recognizing the role of phishing in facilitating ransomware attacks, pages 9 and 10 of the #StopRansomware Guide offers recommendations for protecting credentials. The guide suggests organizations:
Implement phishing-resistant multi-factor authentication (MFA/2FA) for all services.
Consider passwordless MFA that replaces passwords with two or more verification factors (e.g., a fingerprint, facial recognition, device pin, or a cryptographic key).
Implement password protection policies that require unique passwords of at least 15 characters and utilize a password manager.
Store passwords in a secured database and use strong hashing algorithms.
Educate all employees on proper password security in your annual security training, including emphasizing the importance of not reusing passwords and not saving passwords in local files.
Additionally, having an incident response plan to outline roles and responsibilities during a ransomware attack is essential. Security awareness training is crucial to recognize and deter phishing attacks.
Password managers are an effective deterrent against credential theft because they easily enable users to generate strong and unique passwords for each site they visit. This reduces the risk of password reuse and stops people from defaulting to weaker passwords simply because they’re easy to remember. While password managers alone won’t stop all ransomware attacks - a user or users may still fall prey to a phishing attack and divulge their credentials - the scope of the attack will likely be limited because the same password hasn’t been used for multiple accounts.
Password managers, such as Bitwarden, further protect credentials by enabling two-factor authentication (also known as 2FA), which requires authentication from a second device upon login. This is often accomplished through a security key, authenticator app, or via email.
The #StopRansomware Guide cites passwordless MFA, which can further strengthen verification through biometrics (e.g., a fingerprint, facial recognition), a device pin, or a cryptographic key. Recent data found that nearly three in 10 ransomware attacks started with threat actors using a stolen password. Passwordless solutions like passkeys empower individuals and businesses with a more effective deterrent against ransomware attacks by removing weak or reused credentials from the attack surface altogether. Passkeys prevent the reuse of passwords across services or platforms because they are created uniquely for each user and service. Encrypted authentication protocols like WebAuthn, enable passkeys to enhance protection against phishing attacks, one of the most common initiation points for breaches and ransomware attacks. Using a layered security tech stack that incorporates endpoint detection and response (EDR), network monitoring tools, and email filtering solutions alongside anti-malware and antivirus software will strengthen an organization’s resilience to ransomware attacks by minimizing the attack surface across multiple threat vectors.
The public and private sectors continue recognizing the growing momentum toward passwordless technology. In the 2023 Bitwarden Password Decisions Survey, 49% of IT decision-maker respondents said they were deploying or had plans to deploy passwordless technology. Of those utilizing passwordless authentication, 51% are relying on the ‘something you are’ (biometrics, facial recognition, voiceprint) form of passwordless authentication.
Ransomware attacks are complex, and successful mitigation against them requires a multi-layered approach. Password management and passwordless authentication measures create the foundation for a strong security culture, foster better password habits, and empower employees and organizations with the tools they need to strengthen credential security.
Operating system security
Keep operating systems up to date
Keeping operating systems up-to-date is a fundamental step in preventing ransomware attacks. Outdated operating systems inherently create security vulnerabilities that cybercriminals can exploit to gain unauthorized access. Regularly updating device operating systems and ensuring that the latest security patches and features are installed will provide added protection against these threats. Enabling automatic updates is a simple yet effective way to ensure that operating systems remain current, reducing the risk of ransomware attacks exploiting known vulnerabilities.
Harden operating system configurations
Hardening operating system configurations is another critical measure to safeguard against ransomware attacks. This process involves configuring operating systems to minimize the attack surface. Start by disabling unnecessary services and removing unused or unpatched software, which can serve as potential entry points for malicious actors. Configuring firewall rules to block incoming traffic that isn’t essential for operational needs adds another layer of defense. Adopting a zero trust security model can significantly enhance an organization’s security posture by preventing lateral movement or privileged access elevation within the network in case of a ransomware infection. This approach ensures that even if one part of a system is compromised, the threat is contained and cannot spread easily.
Network security measures
Network segmentation
Network segmentation is a vital security measure that can help contain and mitigate the impact of ransomware attacks. By dividing an internal network into smaller, isolated segments, organizations can limit the spread of ransomware if an infection occurs. Each segment should be equipped with its own security controls, including firewalls and access control policies, to prevent unauthorized access. This approach can quickly identify and isolate infected systems while reducing the scalability of a ransomware attack. Implementing network segmentation as part of a broader security strategy can significantly enhance a company's ability to respond to and recover from ransomware incidents, ensuring that critical systems and information remain protected.
Get started with Bitwarden and the zero trust security model
Ready to try out password sharing with Bitwarden? Quickly get started with a free Bitwarden account, or start a 7-day free trial of our business plans to keep your team safe online. Still have questions? Check out the free weekly demo.
