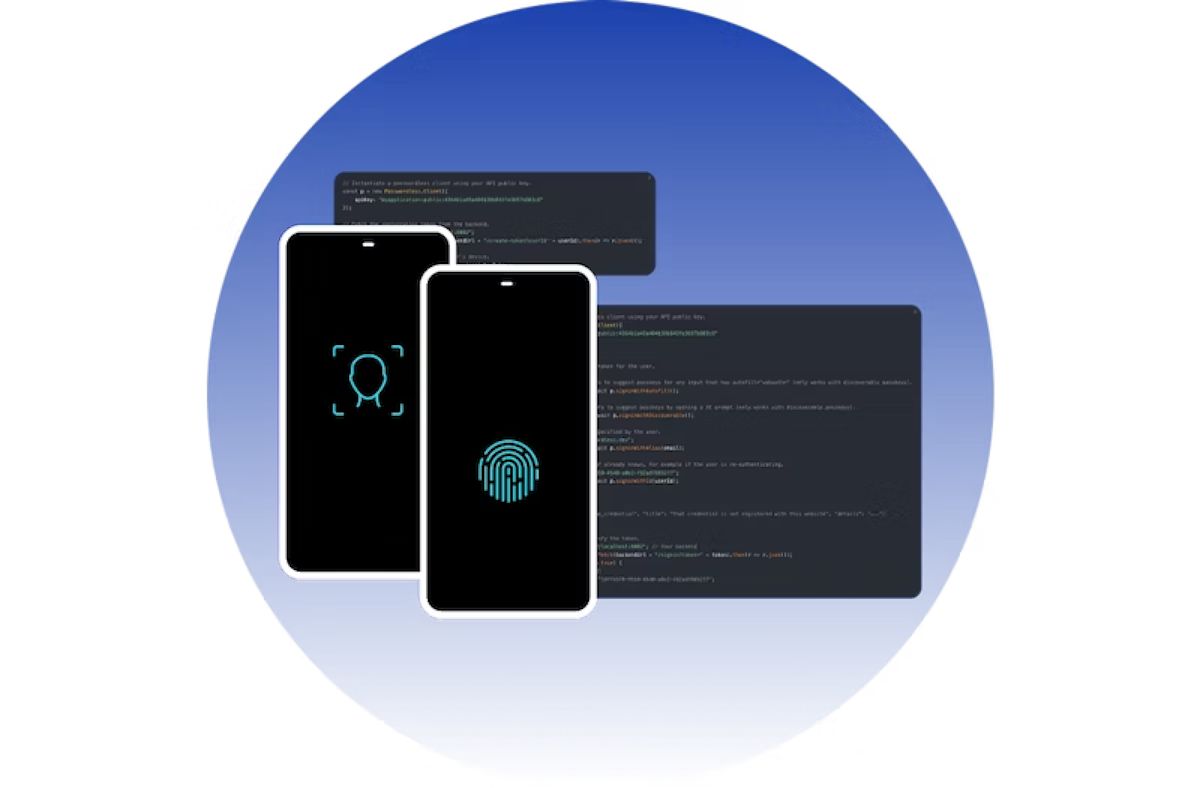
Passwords aren’t the be-all and end-all when it comes to security. Your teams must use strong and unique passwords stored in a password manager AND multi-factor authentication (MFA).
MFA is a security measure that requires you and the members of your team to provide multiple forms of verification to access a system or account, adding an extra layer of protection beyond traditional username and password combinations. MFA typically combines two or more of the following:
Something the user knows (such as a password)
Something the user has (such as a unique code or token)
Something the user is (such as a finger print or facial recognition)
Many people in your organization will recognize and be familiar with MFA since so many consumer apps and websites now offer it, but they might not understand its importance or find the extra step too complicated or a waste of time. Understanding The Why behind MFA is the key to getting buy-in from your team.
The importance of MFA lies in its ability to significantly enhance security by mitigating the risks associated with stolen or weak passwords. Even if an attacker manages to obtain someone’s password, they would still need access to the additional authentication factor to gain entry. This significantly reduces the likelihood of unauthorized access and compromises.
MFA helps protect against various security threats, such as phishing attacks and credential stuffing(when hackers find your password in a breach and try to log into your accounts with it). By requiring an additional layer of verification, MFA adds an extra barrier that makes it more challenging for hackers to impersonate legitimate users. It also provides an early warning system, since any unauthorized attempts to access an account will trigger alerts or require additional verification.
Implementing MFA is crucial, especially for sensitive accounts or systems containing confidential information. It helps prevent unauthorized access, data breaches, brand trust loss, and identity theft. By embracing MFA and by convincing everyone else in your organization to use it, you can significantly bolster security and ensure the protection of valuable company assets.